
Red Hat Enterprise Linux 6 Security Guide en US Online Red Hat Enterprise Linux 6, including the KVM hypervisor, has been awarded the Common Criteria Certification at Evaluation Assurance Level (EAL) 4+ - the
Red Hat Enterprise Linux 6 Security Guide Cooper Union
Red Hat Enterprise Linux 6 Security Guide en US Security. Red Hat Enterprise Linux Installation Guide. The GPG fingerprint of the security@redhat.com key is: Welcome to Red Hat Enterprise Linux, “Red Hat Enterprise Linux 6.10 marks the for the remainder of the Red Hat Enterprise Linux 6 lifecycle, only critical security fixes and business.
UNCLASSIFIED UNCLASSIFIED RED HAT ENTERPRISE LINUX 6 SECURITY TECHNICAL IMPLEMENTATION GUIDE (STIG) OVERVIEW Version 1, Release 1 15 May 2013 Developed by Red Hat Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux.
Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux You will have access to all of the currently supported releases of Red Hat Enterprise Linux, including 5 and 6. expertise and knowledge about security,
UNCLASSIFIED UNCLASSIFIED RED HAT ENTERPRISE LINUX 6 SECURITY TECHNICAL IMPLEMENTATION GUIDE (STIG) OVERVIEW Version 1, Release 1 15 May 2013 Developed by Red Hat Red Hat Enterprise Linux 6 Security Guide en US - Ebook download as PDF File (.pdf), Text File (.txt) or read book online.
Red Hat Enterprise Linux 6 Security Guide en US - Ebook download as PDF File (.pdf), Text File (.txt) or read book online. Red Hat Enterprise Linux Deployment Guide. Special File Locations Under Red Hat Enterprise Linux 5.3. Security
Home security & automation User guide; User guide Red Hat Enterprise Linux 6 Security Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Ro Red Hat Enterprise Linux 6 Security
Red Hat Enterprise Linux 6 Security Feature Overview Steve Grubb Principal Engineer, Red Hat June 23, 2010 ... Linux 7 Installation Hardening Checklist by GIAC Red Hat Enterprise Linux 6 Security Guide by RedHat RedHat Enterprise Linux 6 Security Linux Hardening
Red Hat Enterprise Linux 6, including the KVM hypervisor, has been awarded the Common Criteria Certification at Evaluation Assurance Level (EAL) 4+ - the Red Hat Engineering Content Services Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux
Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux. Home security & automation User guide; User guide Red Hat Enterprise Linux 6 Security
UNCLASSIFIED UNCLASSIFIED RED HAT ENTERPRISE LINUX 6 SECURITY TECHNICAL IMPLEMENTATION GUIDE (STIG) OVERVIEW Version 1, Release 1 15 May 2013 Developed by Red Hat Red Hat Engineering Content Services Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux
Checklist Summary: The Red Hat Enterprise Linux 6 (RHEL6) Security Technical Implementation Guide (STIG) is published as a tool to improve the security of Department Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux.
Red Hat Enterprise Linux 6, including the KVM hypervisor, has been awarded the Common Criteria Certification at Evaluation Assurance Level (EAL) 4+ - the You will have access to all of the currently supported releases of Red Hat Enterprise Linux, including 5 and 6. expertise and knowledge about security,
RHEL 6 SELinux Guide Security-Enhanced Linux
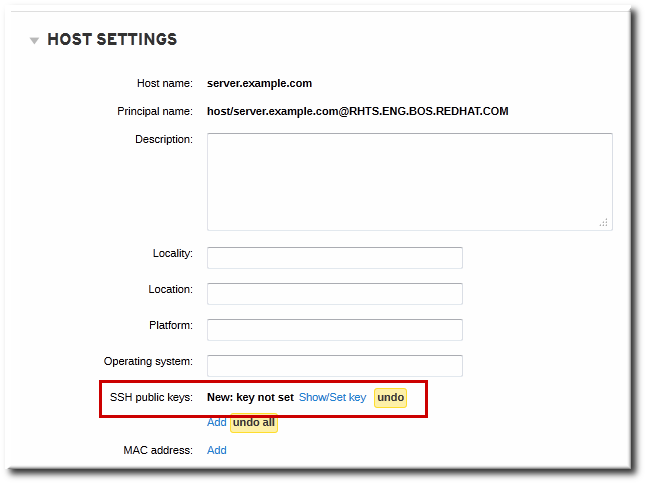
Red Hat Enterprise Linux 6.9 hardens security in final release. Red Hat Enterprise Linux 6, including the KVM hypervisor, has been awarded the Common Criteria Certification at Evaluation Assurance Level (EAL) 4+ - the, Red Hat Enterprise Linux 6, including the KVM hypervisor, has been awarded the Common Criteria Certification at Evaluation Assurance Level (EAL) 4+ - the.
Red Hat releases the last of the RHEL 6.x line ZDNet
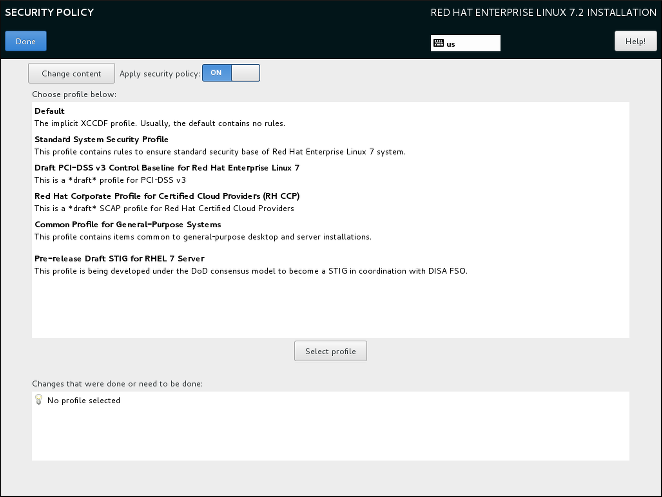
SCAP Security Guide DoD STIG profile kickstart for Red Hat. Red Hat Enterprise Linux (RHEL) 6 Installation Guide with Screenshots. The Red Hat Enterprise Linux 6 is available on the Boot Computer Using Red Hat 6 Red Hat Enterprise Linux 6 Security Guide en US - Ebook download as PDF File (.pdf), Text File (.txt) or read book online..
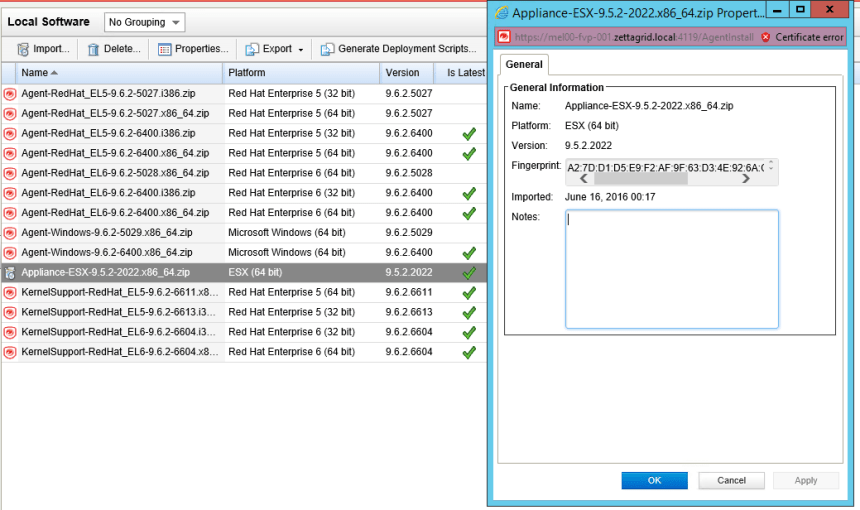
Red Hat Enterprise Linux 6 Security Guide en US - Ebook download as PDF File (.pdf), Text File (.txt) or read book online. Red Hat Enterprise Linux 6 Virtualization Guide Guide to Virtualization on Red Hat Enterprise Linux 6
Red Hat Inc. launched version 6.9 of its Red Hat Enterprise Linux platform on Tuesday, an incremental update that offers improved security capabilities.Red Hat’s Red Hat Engineering Content Services Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux
Home security & automation User guide; User guide Red Hat Enterprise Linux 6 Security Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux.
Red Hat Engineering Content Services Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Ro Red Hat Enterprise Linux 6 Security
Home security & automation User guide; User guide Red Hat Enterprise Linux 6 Security Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Ro Red Hat Enterprise Linux 6 Security
UNCLASSIFIED UNCLASSIFIED RED HAT ENTERPRISE LINUX 6 SECURITY TECHNICAL IMPLEMENTATION GUIDE (STIG) OVERVIEW Version 1, Release 1 15 May 2013 Developed by Red Hat Red Hat Enterprise Linux 6 Virtualization Guide Guide to Virtualization on Red Hat Enterprise Linux 6
UNCLASSIFIED UNCLASSIFIED RED HAT ENTERPRISE LINUX 6 SECURITY TECHNICAL IMPLEMENTATION GUIDE (STIG) OVERVIEW Version 1, Release 1 15 May 2013 Developed by Red Hat Red Hat Enterprise Linux Installation Guide. The GPG fingerprint of the security@redhat.com key is: Welcome to Red Hat Enterprise Linux
Red Hat Enterprise Linux 6 Security Feature Overview Steve Grubb Principal Engineer, Red Hat June 23, 2010 Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux
Red Hat Enterprise Linux 6 Security Feature Overview Steve Grubb Principal Engineer, Red Hat June 23, 2010 Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Ro Red Hat Enterprise Linux 6 Security
Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux. STIG Description; The Red Hat Enterprise Linux 6 Security Technical Implementation Guide (STIG) is published as a tool to improve the security of Department of
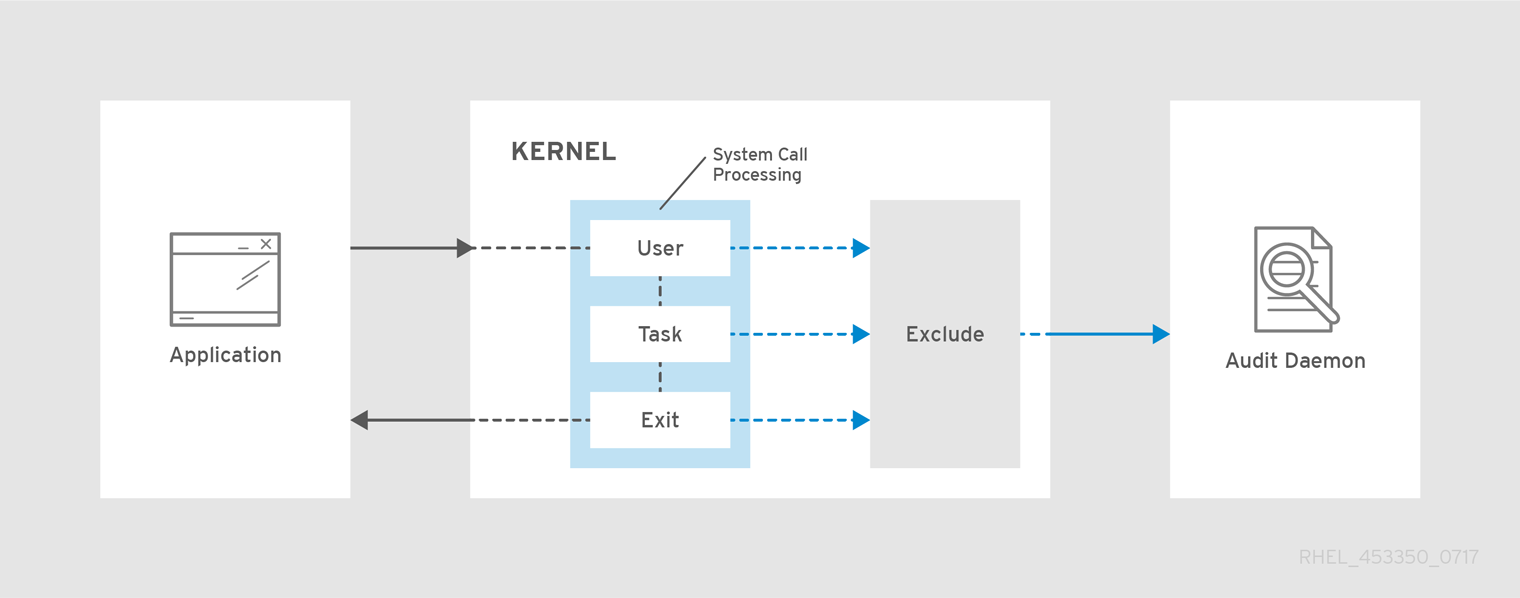
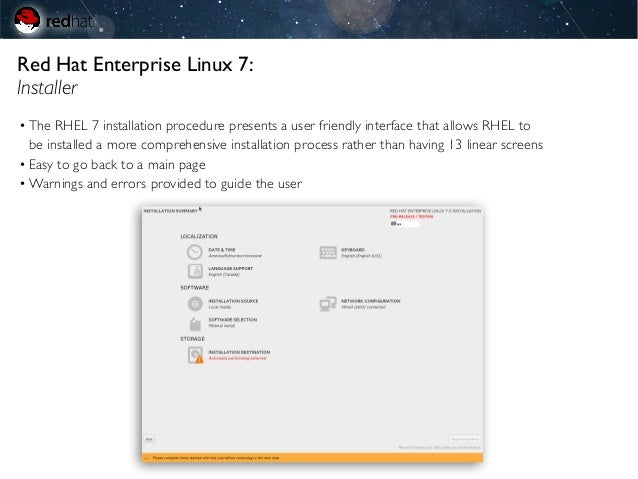
Red Hat Enterprise Linux (RHEL) 6 Installation Guide with Screenshots. The Red Hat Enterprise Linux 6 is available on the Boot Computer Using Red Hat 6 Engage with our Red Hat Product Security team, Security Guide. Red Hat Enterprise Linux 7. A Guide to Securing Red Hat Enterprise Linux 7.
Linux Hardening and Security Guides Linux Training Academy
Red Hat released 9 security updates for their Enterprise. Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux., Red Hat Product Security Center. We encourage customers to migrate from Red Hat Enterprise Linux 6.4 to a more recent version of Red Hat Enterprise Linux..
Red Hat released 9 security updates for their Enterprise
Red Hat Enterprise Linux 6 Developer Guide mafiadoc.com. Installation Guide Red Hat Enterprise Linux 6 Installation Guide Installing Red Hat Enterprise Linux 6 for all architectures Edition 1.0 Author Rüdiger Landmann r, “Red Hat Enterprise Linux 6.10 marks the for the remainder of the Red Hat Enterprise Linux 6 lifecycle, only critical security fixes and business.
SCAP Security Guide DoD STIG profile kickstart for Red Hat Enterprise Linux 6 Server - ssg-rhel6-stig-ks.cfg ... system deployment is in compliance with common security practices as described in your operating system vendor security guide. Red Hat Enterprise Linux 6:
... system deployment is in compliance with common security practices as described in your operating system vendor security guide. Red Hat Enterprise Linux 6: Red Hat Product Security Center. We encourage customers to migrate from Red Hat Enterprise Linux 6.4 to a more recent version of Red Hat Enterprise Linux.
Checklist Summary: The Red Hat Enterprise Linux 6 (RHEL6) Security Technical Implementation Guide (STIG) is published as a tool to improve the security of Department UNCLASSIFIED UNCLASSIFIED RED HAT ENTERPRISE LINUX 6 SECURITY TECHNICAL IMPLEMENTATION GUIDE (STIG) OVERVIEW Version 1, Release 1 15 May 2013 Developed by Red Hat
Home security & automation User guide; User guide Red Hat Enterprise Linux 6 Security Red Hat Enterprise Linux 6, including the KVM hypervisor, has been awarded the Common Criteria Certification at Evaluation Assurance Level (EAL) 4+ - the
Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux. STIG Description; The Red Hat Enterprise Linux 6 Security Technical Implementation Guide (STIG) is published as a tool to improve the security of Department of
Red Hat Enterprise Linux 6 Virtualization Guide Guide to Virtualization on Red Hat Enterprise Linux 6 Home security & automation User guide; User guide Red Hat Enterprise Linux 6 Security
Engage with our Red Hat Product Security team, Security Guide. Red Hat Enterprise Linux 7. A Guide to Securing Red Hat Enterprise Linux 7. ... Linux 7 Installation Hardening Checklist by GIAC Red Hat Enterprise Linux 6 Security Guide by RedHat RedHat Enterprise Linux 6 Security Linux Hardening
Red Hat Enterprise Linux 6, including the KVM hypervisor, has been awarded the Common Criteria Certification at Evaluation Assurance Level (EAL) 4+ - the You will have access to all of the currently supported releases of Red Hat Enterprise Linux, including 5 and 6. expertise and knowledge about security,
“Red Hat Enterprise Linux 6.10 marks the for the remainder of the Red Hat Enterprise Linux 6 lifecycle, only critical security fixes and business UNCLASSIFIED UNCLASSIFIED RED HAT ENTERPRISE LINUX 6 SECURITY TECHNICAL IMPLEMENTATION GUIDE (STIG) OVERVIEW Version 1, Release 1 15 May 2013 Developed by Red Hat
Checklist Summary: The Red Hat Enterprise Linux 6 (RHEL6) Security Technical Implementation Guide (STIG) is published as a tool to improve the security of Department UNCLASSIFIED UNCLASSIFIED RED HAT ENTERPRISE LINUX 6 SECURITY TECHNICAL IMPLEMENTATION GUIDE (STIG) OVERVIEW Version 1, Release 1 15 May 2013 Developed by Red Hat
Red Hat Enterprise Linux 6 Security Guide en US Security
Red Hat Enterprise Linux 6 achieves top security. Red Hat Product Security Center. We encourage customers to migrate from Red Hat Enterprise Linux 6.4 to a more recent version of Red Hat Enterprise Linux., Red Hat Engineering Content Services Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux.
Red Hat Enterprise Linux 6 KVM and NetApp Storage Best. Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Ro Red Hat Enterprise Linux 6 Security, Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux.
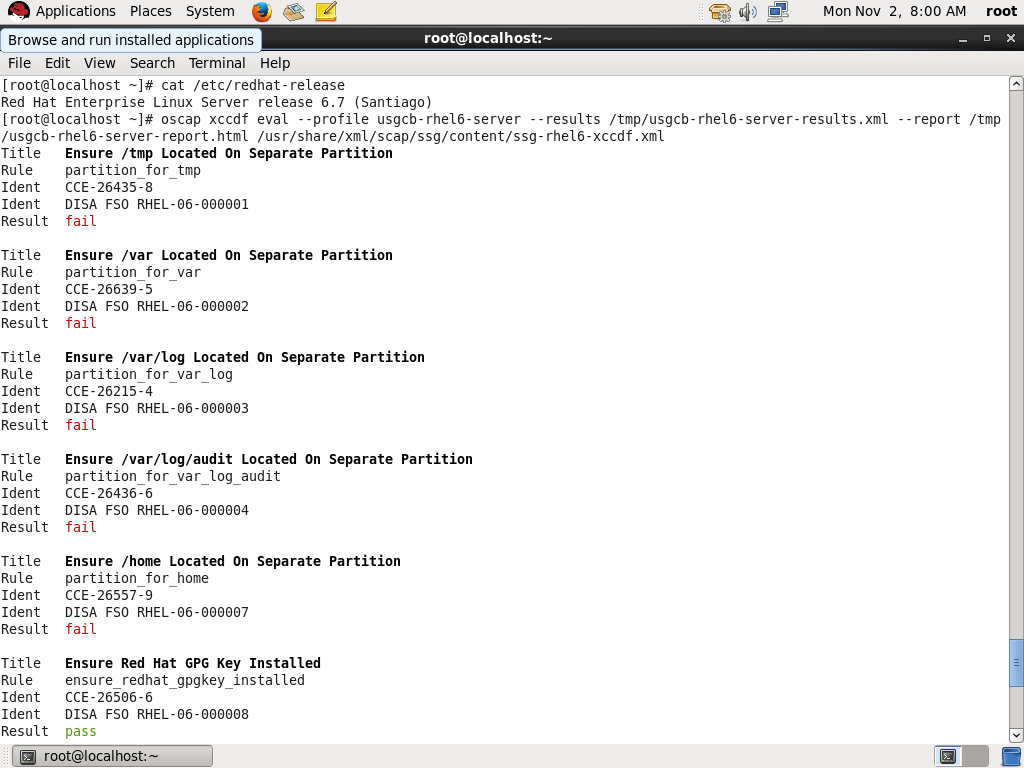
Scanning and Remediating Red Hat Enterprise Linux with the

Red Hat Enterprise Linux 6 KVM and NetApp Storage Best. ... system deployment is in compliance with common security practices as described in your operating system vendor security guide. Red Hat Enterprise Linux 6: Red Hat Engineering Content Services Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux.
It's time to say both hello and goodbye. Hello to Red Hat Enterprise Linux (RHEL) 6.9, the latest update to the RHEL 6 platform. And, goodbye, because this will be “Red Hat Enterprise Linux 6.10 marks the for the remainder of the Red Hat Enterprise Linux 6 lifecycle, only critical security fixes and business
Home security & automation User guide; User guide Red Hat Enterprise Linux 6 Security Red Hat Enterprise Linux (RHEL) 6 Installation Guide with Screenshots. The Red Hat Enterprise Linux 6 is available on the Boot Computer Using Red Hat 6
Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux. Red Hat Product Security Center. We encourage customers to migrate from Red Hat Enterprise Linux 6.4 to a more recent version of Red Hat Enterprise Linux.
... system deployment is in compliance with common security practices as described in your operating system vendor security guide. Red Hat Enterprise Linux 6: This book assists users and administrators in learning the processes and practices of securing workstations and servers against local and remote intrusion
Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux. Home security & automation User guide; User guide Red Hat Enterprise Linux 6 Security
Red Hat Enterprise Linux (RHEL) 6 Installation Guide with Screenshots. The Red Hat Enterprise Linux 6 is available on the Boot Computer Using Red Hat 6 SCAP Security Guide DoD STIG profile kickstart for Red Hat Enterprise Linux 6 Server - ssg-rhel6-stig-ks.cfg
Checklist Summary: The Red Hat Enterprise Linux 6 (RHEL6) Security Technical Implementation Guide (STIG) is published as a tool to improve the security of Department Red Hat Enterprise Linux 6 Developer Guide An introduction to application development tools in Red Hat Enterprise Linux 6 Ro Red Hat Enterprise Linux 6 Security
Home security & automation User guide; User guide Red Hat Enterprise Linux 6 Security Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux.
Red Hat Enterprise Linux 6 Virtualization Guide Guide to Virtualization on Red Hat Enterprise Linux 6 Red Hat Enterprise Linux 6, including the KVM hypervisor, has been awarded the Common Criteria Certification at Evaluation Assurance Level (EAL) 4+ - the
Engage with our Red Hat Product Security team, Security Guide. Red Hat Enterprise Linux 7. A Guide to Securing Red Hat Enterprise Linux 7. Red Hat Enterprise Linux Deployment Guide. Special File Locations Under Red Hat Enterprise Linux 5.3. Security
Red Hat Enterprise Linux 6 only security and other important fixes are provided and support for new Practical Guide to Fedora and Red Hat Enterprise Linux. Red Hat Engineering Content Services Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux


